A stability flaw in the way Microsoft Windows guards people from destructive data files was actively exploited in malware assaults for two several years prior to previous 7 days, when Microsoft ultimately issued a software program update to appropriate the challenge.
Just one of the 120 protection holes Microsoft fixed on Aug. 11’s Patch Tuesday was CVE-2020-1464, a issue with the way every supported variation of Home windows validates electronic signatures for computer system applications.
Code signing is the technique of making use of a certificate-based electronic signature to indication executable files and scripts in buy to verify the author’s id and ensure that the code has not been improved or corrupted considering the fact that it was signed by the writer.
Microsoft mentioned an attacker could use this “spoofing vulnerability” to bypass protection functions supposed to stop improperly signed documents from staying loaded. Microsoft’s advisory helps make no point out of stability scientists getting told the firm about the flaw, which Microsoft acknowledged was actively remaining exploited.
In point, CVE-2020-1464 was initially spotted in assaults utilized in the wild again in August 2018. And numerous scientists educated Microsoft about the weakness above the earlier 18 months.
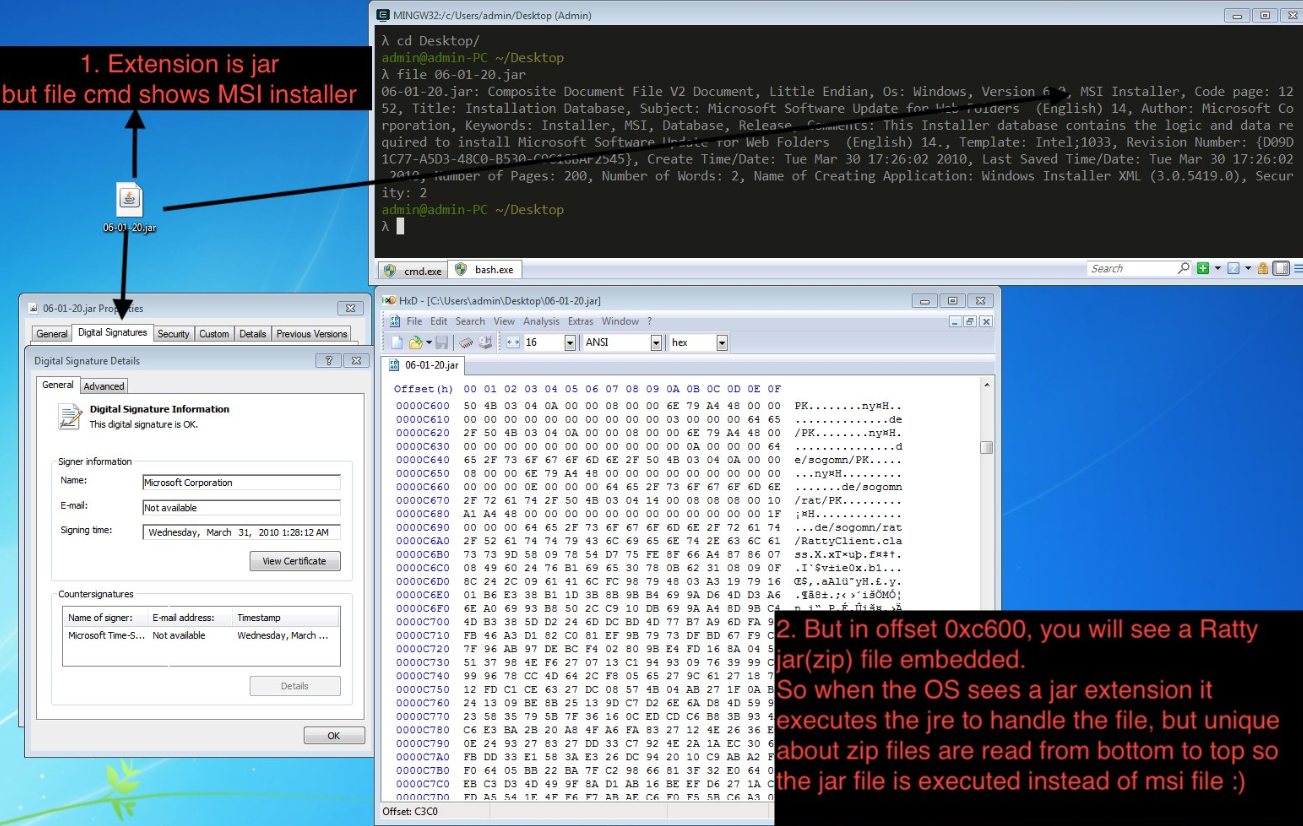
Bernardo Quintero is the manager at VirusTotal, a services owned by Google that scans any submitted files towards dozens of antivirus companies and displays the effects. On Jan. 15, 2019, Quintero published a site post outlining how Home windows retains the Authenticode signature legitimate immediately after appending any written content to the finish of Windows Installer data files (people ending in .MSI) signed by any software package developer.
Quintero claimed this weak spot would notably acute if an attacker ended up to use it to disguise a destructive Java file (.jar). And, he said, this precise assault vector was in truth detected in a malware sample despatched to VirusTotal.
“In brief, an attacker can append a destructive JAR to a MSI file signed by a trusted software program developer (like Microsoft Company, Google Inc. or any other very well-acknowledged developer), and the ensuing file can be renamed with the .jar extension and will have a legitimate signature in accordance Microsoft Windows,” Quintero wrote.
But in accordance to Quintero, even though Microsoft’s protection crew validated his conclusions, the corporation chose not to address the difficulty at the time.
“Microsoft has resolved that it will not be repairing this issue in the existing variations of Windows and agreed we are capable to weblog about this scenario and our results publicly,” his blog submit concluded.
Tal Be’ery, founder of Zengo, and Peleg Hadar, senior protection researcher at SafeBreach Labs, penned a website put up on Sunday that pointed to a file uploaded to VirusTotal in August 2018 that abused the spoofing weakness, which has been dubbed GlueBall. The previous time that August 2018 file was scanned at VirusTotal (Aug 14, 2020), it was detected as a malicious Java trojan by 28 of 59 antivirus systems.
Much more just lately, other people would furthermore call consideration to malware that abused the security weak spot, which includes this write-up in June 2020 from the Safety-in-bits website.
Be’ery explained the way Microsoft has dealt with the vulnerability report would seem rather odd.
“It was very crystal clear to everybody included, Microsoft involved, that GlueBall is indeed a legitimate vulnerability exploited in the wild,” he wrote. “Therefore, it is not distinct why it was only patched now and not two many years in the past.”
Questioned to remark on why it waited two decades to patch a flaw that was actively getting exploited to compromise the protection of Home windows personal computers, Microsoft dodged the question, declaring Windows customers who have utilized the most current security updates are protected from this assault.
“A protection update was introduced in August,” Microsoft explained in a prepared assertion sent to KrebsOnSecurity. “Customers who apply the update, or have computerized updates enabled, will be shielded. We keep on to stimulate shoppers to convert on automated updates to assist ensure they are protected.”
Update, 12:45 a.m. ET: Corrected attribution on the June 2020 blog short article about GlueBall exploits in the wild.
Tags: Bernardo Quintero, CVE-2020-1464, GlueBall, Peleg Hadar, SafeBreach Labs, Securityinbits.com, Tal Be’ery, Zengo

Freelance twitter maven. Infuriatingly humble coffee aficionado. Amateur gamer. Typical beer fan. Avid music scholar. Alcohol nerd.