Most phishing attacks come from emails that appear to have come from a bank. There is a problem with the account, it says, and the account is in danger of being closed with costs. The victims are then asked to click on a link, says Declan Hiscox from Watchlist Internet: “But you don’t actually go to the bank’s website, but to a fake page that only looks like it.” Your own login data ends up being then passed directly to the criminals, according to Hiscox.
Current operating system and regular updates
E-mail isn’t usually dangerous as long as it’s in the inbox, says Hiscox. Even if you click on the link and land on the fake page of criminals, you still need not panic. At least not if the current operating system is installed and all security-related updates have been installed. Incidentally, this applies to PCs as well as smartphones and other mobile devices.
On the other hand, if you use an older operating system or don’t have any updates, it would theoretically be possible for attackers to exploit the security gap. In such a case, simply accessing the fraudulent website may result in unnoticed malware loading on the computer. In practice, however, this rarely happens, so there’s no need to worry too much, according to Hiscox.
Banks do not ask for login details
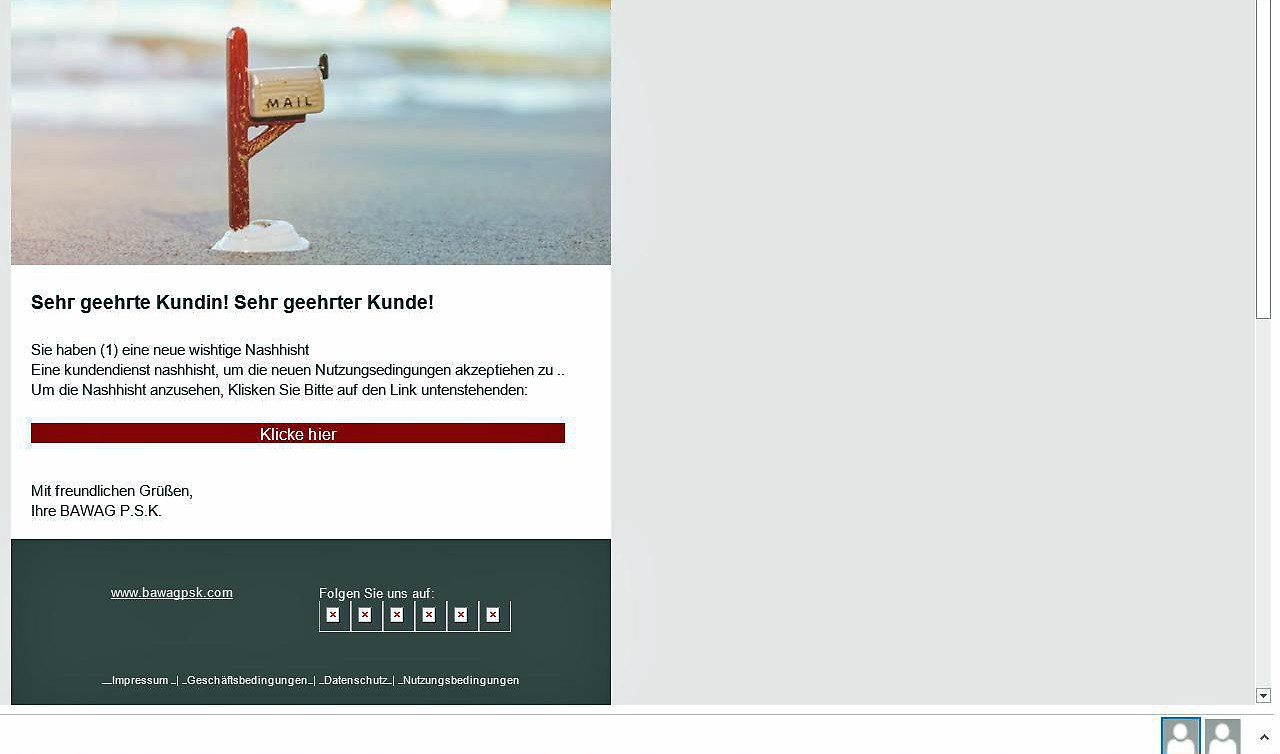
Basically, it can be said that a bank does not send emails to its customers to provide account information through a direct link. At best, you will be informed that, for example, important information may be found in the mailbox of an online account. In such a situation, you have to choose the website of the bank yourself. According to Hiscox, a direct link is a clear indication that fraudsters are at work here. If you follow such links and enter a security code, password or TAN number on the perpetrator’s fake page, the trap is set off. Attackers use this information to gain access to the account.
Note the sender’s address
Phishing e-mails often ask for an app to be installed on a smartphone for security reasons. According to Hiscox, this application is actually dangerous malware that enables attackers to intercept TAN numbers or gain access to real banking apps.
If you get any suspicious e-mail in your inbox, the first thing you should pay attention to is the sender’s address. If it is called “[email protected]”, as in the present case, it should be clear that there is no serious company behind it. However, some fake addresses are also cleverly chosen, for example in such a way that the name of the bank appears in the first part. That’s why you should pay special attention to the part of the e-mail address that can be found after the @ sign. According to Hiscox, this section reveals the domain from which the letter is sent. The front area can be independently defined by fraudsters.
Phone scammers disguising themselves as Microsoft service
In any case, caution is advised; Only on Wednesday did Watchlist Internet warn of an accumulation of such phishing attacks in Austria. Cybercriminals work here on behalf of well-known companies such as EasyBank, Bawg, Volksbank and telecommunications provider Magenta.
The telephone provides another target to capture citizens’ money. It is not uncommon for fraudsters, colloquially known as scammers, to target old landline connections. For example, scammers pretend to be employees of Microsoft service. They fool their victims into believing that malware has been found on the computer and request remote access to the computer to eliminate the alleged virus infection.
Scam hunters prey on cybercriminals
The watchlist internet expert advises that such calls should be terminated immediately and simply disconnected. Scammers are adept at gaining the trust of their victims. For example, by intentionally taking affected people to an area of computer settings in which error messages such as program crashes are registered by default. These messages can be frightening, but they are not intended for users and therefore do not indicate any specific danger, Hiscox says.
Now there are groups like YouTube bloggers and “scam hunters” who have made it their job to hunt down scammers. They, in turn, hack the criminals’ computers and turn the tables. To the delight of the public and the displeasure of the scammers. They are usually furious when they see, for example, money that they painstakingly stole is disappearing from their accounts. However, such scammers are highly specialized hackers, and they mostly achieve their success through random hits.
Lack of cooperation between police officers
Official officials have a hard time with targeted criminal prosecution. The online world is big, the network of criminals is great. Police officers rather short. In principle, it is recommended to report such incidents of online fraud. However, authorities need a large number of solid suspected cases to be able to launch proper investigations and conduct them efficiently. Criminals are usually located abroad, for example in India.
Austrian investigators are therefore dependent on the cooperation of the Indian police and administrative assistance should be requested. A laborious and not always successful process, as international cooperation is often not available. Although Hiscox from Watchlist Internet admits that law enforcement may eventually become more efficient in this area, criminals may still feel relatively safe for the time being. Hiscox says users currently have no choice but to be careful on the Internet.

Freelance twitter maven. Infuriatingly humble coffee aficionado. Amateur gamer. Typical beer fan. Avid music scholar. Alcohol nerd.







